1. The three outputs x1x2x3 from the 8x3 priority encoder are used to provide a vector address of the form 101x1x2x300. What is the second highest priority vector address in hexadecimal if the vector addresses are starting from the one with the highest priority?
(A) BC (B) A4
(C) BD (D) AC
Answer: B
2. What will be the output at PORT1 if the following program is executed?
MVI B, 82H
MOV A, B
MOV C, A
MVI D, 37H
OUT PORT1
HLT
(A) 37H (B) 82H
(C) B9H (D) 00H
Answer: B
Explanation:
In 8085 programming, the result of an operation is stored in the accumulator.
So output is 82H.
3. Which of the following 8085 microprocessor hardware interrupt has the lowest priority?
(A) RST 6.5 (B) RST 7.5
(C) TRAP (D) INTR
Answer: D
4. A dynamic RAM has refresh cycle of 32 times per msec. Each refresh operation requires 100 nsec and a memory cycle requires 250 nsec. What percentage of memory’s total operating time is required for refreshes?
(A) 0.64 (B) 0.96
(C) 2.00 (D) 0.32
Answer: D
Explanation:
in 1ms : refresh = 32 times
Memory cycle = 1ms/250ns = 106ns/250ns = 4000 times
Therefore, % of refresh time = (32 x 100ns)/(4000 x 250ns)
= 3200ns/1000000 x 100% = 0.32%
5. A DMA controller transfers 32-bit words to memory using cycle Stealing. The words are assembled from a device that transmits characters at a rate of 4800 characters per second. The CPU is fetching and executing instructions at an average rate of one million instructions per second. By how much will the CPU be slowed down because of the DMA transfer?
(A) 0.06% (B) 0.12%
(C) 1.2% (D) 2.5%
Answer: B
Explanation:
The DMA combines one word from four consecutive characters (bytes) so we get
4800 chars/s = 4800 bytes/s = 1200 words/s
If we assume that one CPU instruction is one word wide then
1 million instructions/s = 1 million words/s = 106 word/s
So we have 1200 words received during one second and (106-1200) words processed by the CPU (while DMA is transferring a word, the CPU cannot fetch the instruction so we have to subtract the number of words transferred by DMA).
While DMA transfer CPU executes only 106 - 1200 = 998800 instructions
[998800 / 106] * 100 = 99.88 %
Slowdown = 100 - 99.88 = 0.12%
The CPU will be slowed down by 0.12%.
6. A CPU handles interrupt by executing interrupt service subroutine.................
(A) by checking interrupt register after execution of each instruction
(B) by checking interrupt register at the end of the fetch cycle
(C) whenever an interrupt is registered
(D) by checking interrupt register at regular time interval
Answer: A
7. Given the following set of prolog clauses:
father(X, Y):
parent(X, Y),
male(X),
parent(Sally, Bob),
parent(Jim, Bob),
parent(Alice, Jane),
parent(Thomas, Jane),
male(Bob),
male(Jim),
female(Salley),
female(Alice).
How many atoms are matched to the variable ‘X’ before the query
father(X, Jane) reports a Result?
(A) 1 (B) 2
(C) 3 (D) 4
Answer: A
8. Forward chaining systems are ............. where as backward chaining systems are ................
(A) Data driven, Data driven (B) Goal driven, Data driven
(C) Data driven, Goal driven (D) Goal driven, Goal driven
Answer: C
9. Match the following w.r.t. programming languages:
List - I List – II
(a) JAVA (i) Dynamically object oriented
(b) Python (ii) Statically Non-object oriented
(c) Prolog (iii) Statically object oriented
(d) ADA (iv) Dynamically non-object oriented
Codes:
(a) (b) (c) (d)
(A) (iii) (i) (ii) (iv)
(B) (i) (iii) (ii) (iv)
(C) (i) (iii) (iv) (ii)
(D) (ii) (iv) (i) (iii)
Answer: D
10. The combination of an IP address and a port number is known as ...................
(A) network number (B) socket address
(C) subnet mask number (D) MAC address
Answer: B
11. A network with bandwidth of 10 Mbps can pass only an average of 15,000 frames per minute with each frame carrying an average of 8,000 bits. What is the throughput of this network ?
(A) 2 Mbps (B) 60 Mbps
(C) 120 Mbps (D) 10 Mbps
Answer: A
Explanation:
In data transmission, throughput is the amount of data moved successfully from one place to another in a given period of time, and typically measured in bits per second (bps), or in megabits per second (Mbps) or gigabits per second (Gbps).
Here, Throughput = 15000 x 8000/60 = 2 Mbps
12. Consider a subnet with 720 routers. If a three-level hierarchy is choosen with eight clusters, each containing 9 regions of 10 routers, then total number of entries in the routing table is ...................
(A) 25 (B) 27
(C) 53 (D) 72
Answer: A
Explanation:
Each router needs 10 entries for local routers, 8 entries for routing to other regions within its own cluster, and 7 entries for distant clusters, for a total of 25 entries.
13. In a classful addressing, the IP addresses with 0 (zero) as network number:
(A) refers to the current network
(B) refers to broadcast on the local network
(C) refers to broadcast on a distant network
(D) refers to loopback testing
Answer: A
14. In electronic mail, which of the following protocols allows the transfer of multimedia
messages?
(A) IMAP (B) SMTP
(C) POP 3 (D) MIME
Answer: D
15. A device is sending out data at the rate of 2000 bps. How long does it take to send a file of 1,00,000 characters ?
(A) 50 (B) 200
(C) 400 (D) 800
Answer: C
Explanation:
1,00,000 characters = 1,00,000 x 8 bits = 8,00,000 bits
8,00,000 bits/2000 bps = 400 seconds
16. In Activity-Selection problem, each activity i has a start time si and a finish time fi where si≤fi. Activities i and j are compatible if:
(A) si≥fj (B) sj≥fi
(C) si≥fj or sj≥fi (D) si≥fj and sj≥fi
Answer: C
17. Given two sequences X and Y:
X = <a, b, c, b, d, a, b>
Y = <b, d, c, a, b, a>
The longest common subsequence of X and Y is:
(A) <b, c, a> (B) <c, a, b>
(C) <b, c, a, a> (D) <b, c, b, a>
Answer: D
Explanation:
A subsequence is a sequence that can be derived from another sequence by deleting some elements without changing the order of the remaining elements.
A sequence G is said to be a common subsequence of X and Y, if Z is a subsequence of both X and Y.
Here X = <a, b, c, b, d, a, b>, the sequences <b,c,a>, <c,a,b>, <b,c,b,a> are subsequences of X.
Given a second sequence of symbols Y = <b, d, c, a, b, a>, then <b,c,a>, <c,a,b>, <b,c,b,a> are common subsequences to both X and Y.
However, the longest common subsequence of X and Y is <b,c,b,a>.
18. If there are n integers to sort, each integer has d digits and each digit is in the set {1,2, ..., k}, radix sort can sort the numbers in:
(A) O(d n k) (B) O(d nk)
(C) O((d+n)k) (D) O(d(n+k))
Answer: D
19. The solution of the recurrence relation
is :
(A) O(lg n) (B) O(n)
(C) O(n lg n) (D) None of the above
Answer: D
20. Floyd-Warshall algorithm utilizes ............... to solve the all-pairs shortest paths problem on a directed graph in ................ time.
(A) Greedy algorithm, θ(V3) (B) Greedy algorithm, θ(V2 lgn)
(C) Dynamic programming, θ(V3) (D) Dynamic programming, θ(V2 lgn)
Answer: C
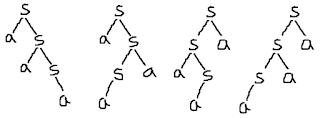
21. Let n=4 and (a1, a2, a3, a4) = (do, if, int, while). Let p(1:4) = (3/8, 3/8, 1/8, 1/8) and q(1:4) = (2/8, 3/8, 1/8, 1/8, 1/8) where p(i) and q(i) denotes the probability with which we search ai and the identifier x being searched satisfy ai < x < ai+1 respectively. The optimal search tree is given by:
Answer: B
22. The family of context sensitive languages is ................. under union and ................. under reversal.
(A) closed, not closed (B) not closed, not closed
(C) closed, closed (D) not closed, closed
Answer: C
23. Match the following :
List - I List - II
(a) {an bn|n > 0} is a deterministic (i) but not recursive language
context free language
(b) The complement of {an bn an|n > 0} (ii) but not context free language
is a context free language
(c) {an bn an} is context sensitive language (iii) but can not be accepted by a deterministic pushdown automation
(d) L is a recursive language (iv) but not regular
Codes :
(a) (b) (c) (d)
(A) (i) (ii) (iii) (iv)
(B) (i) (ii) (iv) (iii)
(C) (iv) (iii) (ii) (i)
(D) (iv) (iii) (i) (ii)
Answer: Marks to all
24. The language of all non-null strings of a’s can be defined by a context free grammar as
follow :
S→a S|S a| a
The word a3 can be generated by ................ different trees.
(A) Two (B) Three
(C) Four (D) Five
Answer: C
Explanation:
25. Which one of the following non-functional quality attributes is not highly affected by the
architecture of the software ?
(A) Performance (B) Reliability
(C) Usability (D) Portability
Answer: C
26. The context free grammar given by
S→XYX
X→aX|bX|λ
Y→bbb
generates the language which is defined by regular expression:
(A) (a+b)*bbb (B) abbb(a+b)*
(C) (a+b)*(bbb)(a+b)* (D) (a+b)(bbb)(a+b)*
Answer: C
27. There are exactly ................ different finite automata with three states x, y and z over the alphabet {a, b} where x is always the start state.
(A) 64 (B) 256
(C) 1024 (D) 5832
Answer: D
28. Given the following two languages :
L1={anban|n>0}
L2={anbanbn+1|n>0}
Which of the following is correct?
(A) L1 is context free language and L2 is not context free language
(B) L1 is not context free language and L2 is context free language
(C) Both L1 and L2 are context free languages
(D) Both L1 and L2 are not context free languages
Answer: A
29. Which of the following is used to make an Abstract class ?
(A) Making atleast one member function as pure virtual function
(B) Making atleast one member function as virtual function
(C) Declaring as Abstract class using virtual keyword
(D) Declaring as Abstract class using static keyword
Answer: A
30. Match the following with reference to object oriented modelling :
List - I List - II
(a) Polymorphism (i) Picking both operator and attributes with
operations appropriate to model an object
(b) Inheritance (ii) Hiding implementation details of methods
from users of objects
(c) Encapsulation (iii) Using similar operations to do similar things
(d) Abstraction (iv) Create new classes from existing class
Codes :
(a) (b) (c) (d)
(A) (iv) (iii) (i) (ii)
(B) (iii) (iv) (i) (ii)
(C) (iii) (i) (ii) (iv)
(D) (iv) (iii) (ii) (i)
Answer: B
31. In CRC based design, a CRC Team consists of :
(a) one or two users representatives
(b) several programmers
(c) project co-ordinators
(d) one or two system analysts
Codes :
(A) (a) and (c) (B) (a), (b), (c) and (d)
(C) (a), (c) and (d) (D) (a), (b) and (d)
Answer: C
32. The end points of a given line are (0, 0) and (6, 18). Compute each value of y as x steps from 0 to 3, by using equation of straight line :
(A) For x=0, y=0; x=1, y=3; x=2, y=6; x=3, y=9
(B) For x=0, y=1; x=1, y=3; x=2, y=4; x=3, y=9
(C) For x=0, y=2; x=1, y=3; x=2, y=6; x=3, y=9
(D) For x=0, y=0; x=1, y=3; x=2, y=4; x=3, y=6
Answer: A
33. Which of the following graphic primitives are considered as the basic building blocks of
computer graphics ?
(a) Points (b) Lines (c) Polylines (d) Polygons
Codes :
(A) (a) only (B) (a) and (b)
(C) (a), (b) and (c) (D) (a), (b), (c) and (d)
Answer: B
34. Javascript and Java has similar name because .................... is/are true.
(a) Javascripts syntax is loosely based on Java’s syntax
(b) Javascript is stripped down version of Java
(c) Java and Javascript are originated from Island of Java
Codes :
(A) (a) only (B) (a), (b) and (c)
(C) (a) and (b) (D) (a) and (c)
Answer: A
35. Which of the following statements are true with reference to the way of describing XML
data ?
(a) XML uses DTD to describe the data
(b) XML uses XSL to describe the data
(c) XML uses a description node to describe the data
Codes :
(A) (a) only (B) (b) only
(C) (a) and (b) (D) (a) and (c)
Answer: D
36. Which of the following is/are correct with reference to Abstract class and interface ?
(a) A class can inherit only one Abstract class but may inherit several interfaces.
(b) An Abstract class can provide complete and default code but an interface has no code.
Codes :
(A) (a) is true (B) (b) is true
(C) Both (a) and (b) are true (D) Neither (a) nor (b) is true
Answer: C
37. Match the following with respect to various memory management algorithms :
List - I List - II
(a) Demand paging (i) degree of multiprogramming
(b) Segmentation (ii) working set
(c) Dynamic partitions (iii) supports user view of memory
(d) Fixed partitions (iv) compaction
Codes :
(a) (b) (c) (d)
(A) (iii) (iv) (ii) (i)
(B) (ii) (iii) (i) (iv)
(C) (iv) (iii) (ii) (i)
(D) (ii) (iii) (iv) (i)
Answer: D
38. Function of memory management unit is :
(A) Address translation (B) Memory allocation
(C) Cache management (D) All of the above
Answer: A
39. Consider a system with twelve magnetic tape drives and three processes P1, P2 and P3. Process P1 requires maximum ten tape drives, process P2 may need as many as four tape drives and P3 may need upto nine tape drives. Suppose that at time t1, process P1 is holding five tape drives, process P2 is holding two tape drives and process P3 is holding three tape drives. At time t1, system is in:
(A) safe state (B) unsafe state
(C) deadlocked state (D) starvation state
Answer: B
40. In Unix operating system, special files are used to :
(A) buffer data received in its input from where a process reads
(B) provide a mechanism to map physical device to file names
(C) store list of file names plus pointers associated with i-nodes
(D) store information entered by a user application program or utility program
Answer: B
NEXT>>>>>

 August 01, 2017
August 01, 2017